To detect whaling phishing attacks, monitor for sophisticated, targeted email threats and train executives in security awareness. Implement advanced email filtering solutions and establish strict verification processes to protect your business.
In the evolving landscape of cyber threats, whaling phishing poses significant risks to organizations. This high-level attack strategy targets top-tier executives with meticulously crafted scams, often masquerading as legal subpoenas, customer complaints, or executive issues. Typical cybersecurity measures may fall short against these personalized threats.
Therefore, enhancing your defense strategy is crucial. Businesses must prioritize cybersecurity education among their leadership and invest in robust email security features. Tailored awareness programs, alongside technology-driven defenses, can be the shield that safeguards your company’s most valuable assets – its data and its people. Effective whaling phishing detection and protection require a combination of informed human vigilance and cutting-edge technological safeguards.
Credit: www.stamus-networks.com
The Menace Of Whaling Phishing
Whaling phishing targets top-level executives within organizations. Unlike typical phishing that often targets larger groups, whaling scams foc-us on high-ranking officials to gain confidential information or financial gains. These sophisticated attacks are personalized to the victim and often involve in-depth research by the attackers to seem legitimate.
The impact on businesses can be severe and wide-ranging. Executives who fall prey to whaling can inadvertently disclose sensitive corporate information, leading to significant financial loss and damage to the company’s reputation. Implementing strong security measures and educating employees, especially those in key positions, about the signs of a whaling attack are crucial steps in protecting a business.
Signals Of A Whaling Attack
Whaling attacks target high-level employees. Email communication often reveals these attacks. Look for unexpected requests for confidential information.
| Signal | Description |
|---|---|
| Email source | Check sender’s email address for slight misspellings. |
| Content Anomalies | Grammar mistakes and unfamiliar language are red flags. |
| Urgency and Confidentiality | Alarm bells should ring with urgent and secret requests. |
Analyze every email for signs of whaling. A legitimate request rarely feels rushed. Never be afraid to double-check the authenticity of suspicious demands. Your business’s safety is paramount.
Establishing A Human Firewall
Training employees is vital in building a human firewall against phishing. Deploying security awareness programs helps staff spot whaling attempts. Interactive courses can sharpen their skills in detecting suspicious emails.
Make these programs regular and engaging. Use simulated phishing attacks to test their knowledge. Teams learn best with hands-on experience. Rewards for spotting phishing can boost participation and vigilance.
Update training materials often due to ever-evolving phishing tactics. Clear communication about the latest threats is crucial. Education must include the importance of reporting potential attacks quickly.
No table needed as the content does not lend itself to a tabular format for this specific subheading.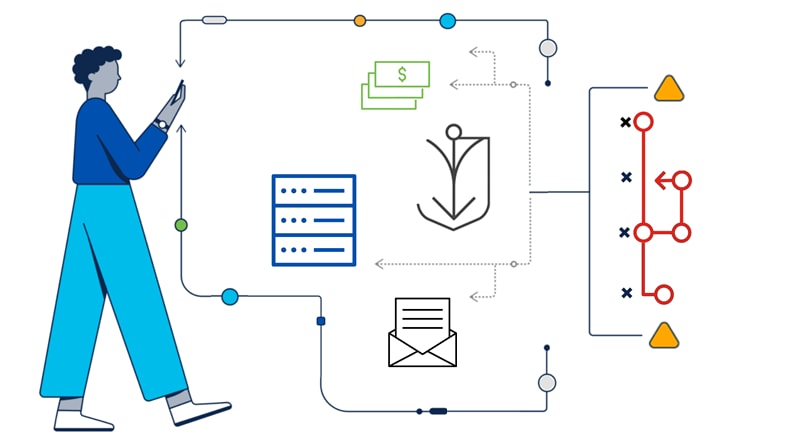
Credit: www.cisco.com
Strengthening Technical Defenses
Email Filtering and Authentication Protocols play a crucial role in guarding against whaling phishing attacks. Utilizing advanced email filtering systems can help to intercept deceptive emails before they reach user inboxes. It’s equally important to set up Email Authentication Protocols such as DMARC, DKIM, and SPF. These protocols verify that the messages are from a legitimate source.
Multi-Factor Authentication (MFA) adds an extra security layer. Users must provide two or more verification forms to access their accounts. This method significantly reduces the risk of unauthorized access, even if login details get stolen.
Conduct Regular Security Audits and Penetration Testing to find system weaknesses. Professional teams mimic cyber-attacks during penetration testing. Through these rigorous tests, businesses can discover and fix security gaps promptly.
In Case Of A Breach: Response And Recovery
Experiencing a security breach demands immediate action to minimize damage. Create an incident response plan before any breaches occur. This plan should detail specific steps for identifying the nature and scope of the breach. It must include contacting legal authorities and communicating with stakeholders.
After addressing the immediate threat, conduct a thorough analysis to understand how the breach happened. Use this insight to reinforce your system’s security. Update cybersecurity measures and protocols regularly. Train staff to recognize and respond to future phishing attempts. Ensuring continuous education on security trends is essential for prevention.
Proactive Strategies To Prevent Whaling Phishing
Businesses must prioritize secure communication to fend off whaling phishing attacks. Email encryption and two-factor authentication greatly enhance security. Employees should be educated to question unexpected high-stake requests, even from senior executives.
Artificial Intelligence (AI) and Machine Learning (ML) offer another layer of defense. These technologies identify and flag anomalous behavior in communications, catching deceitful attempts early. Companies need to continually update their AI models for optimal protection.
Forge partnerships with cybersecurity experts to stay ahead. These professionals provide crucial insights and the latest tactics to intercept phishing schemes. Collaborating with specialists equips businesses with advanced tools and knowledge to counter sophisticated threats.

Credit: www.waident.com
Conclusion
Protecting your enterprise from sophisticated whaling attacks is vital. Implement robust security measures and educate your staff regularly. Stay vigilant, update your defense strategies, and you’ll forge a formidable shield against these phishing threats. Safeguarding your business’s data and reputation starts with awareness and ends with action.
Stay safe, stay secure.







:max_bytes(150000):strip_icc()/renting-vs-owning-home-pros-and-cons.asp-ADD-V2-2ce9de919eb94f62bd4e4c7a23010852.jpg)

